In recent years, the global struggle against the rising menace of money laundering has engaged the attention of financial institutions, law enforcement agencies, and governments around the globe. As the interconnectivity of financial systems continues to grow, those engaged in fraudulent schemes are increasingly employing money laundering tactics to legalize their ill-gotten gains. Recognizing the nature of these criminal phenomena is imperative for policymakers, law enforcement, and the general public alike. This collective understanding is essential as they work together to bolster defenses against financial wrongdoing in a constantly evolving landscape.
The Defrauding Process
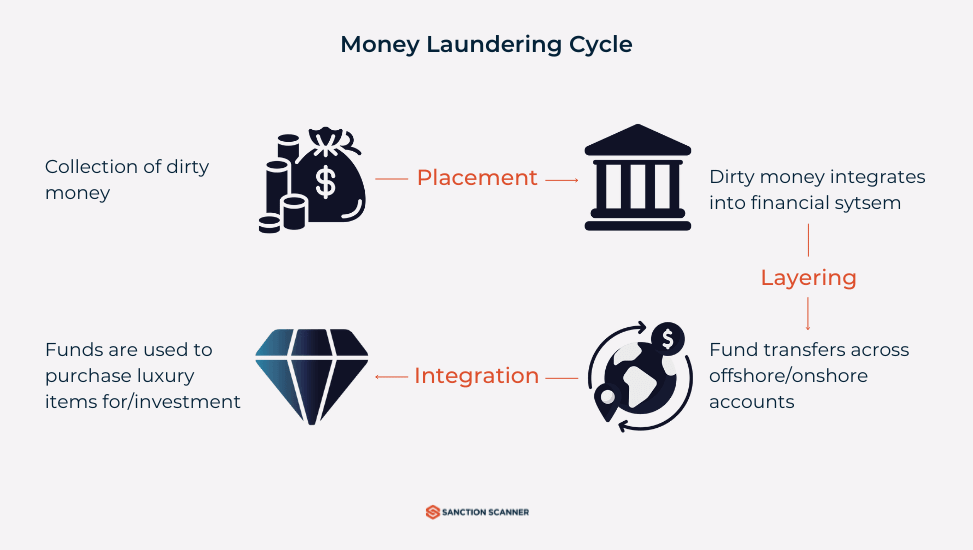
Money laundering progresses through three distinct stages. Initiated as "Placement," the first phase involves introducing unlawfully obtained funds into the financial system. This step relieves the criminal of large amounts of suspicious funds while integrating the money into the legitimate financial framework. However, this initial placement exposes money launderers to heightened vulnerability, as the significant influx of funds into the legitimate system may raise suspicions, increasing the risk of detection.
Subsequent to the Placement stage is the intricate "Layering" process, also referred to as "structuring." This post-placement stage is marked by complex financial transactions, often transcending international borders. The primary goal here is to sever the connection between the illicit funds and their criminal source. Layering comprises a sophisticated series of financial maneuvers devised to obscure the audit trail, effectively breaking the link with the original criminal activity.
In the concluding stage, named "Integration”, the funds are reintroduced into the financial system from what seems to be a legitimate source. The criminal funds, initially introduced as cash and subjected to a series of intricate financial transactions, are now fully assimilated into the financial system. This integration facilitates the use of laundered money for any legitimate purpose, thus completing the cycle of financial deception.
6 Common Types of Defrauding
While there are many tactics employed to launder money, six prevalent types can be noted, each serving as a conduit for defrauding unsuspecting entities. By exploring each of these approaches, the nuanced maneuvers employed by criminals can be understood, enabling organizations and authorities to bolster their defenses against these multifaceted practices.
1. Creating Shell Companies
Shell companies can be defined as corporations strategically crafted to obscure or hide the assets of another entity. These entities, existing solely on paper, lack a physical presence, staff, revenue, or significant assets, yet may hold bank accounts or investments. Although the quick and cost-effective establishment of shell companies is permissible within the legal and financial framework for legitimate purposes, they often serve more dubious ends, especially to launder money. The veil of secrecy surrounding Ultimate Beneficial Ownership (UBO) facilitates the swift creation of shell companies, transforming them into tools for concealing illicit funds, sidestepping sanctions, and eluding anti-money laundering (AML) measures.
The revelation of widespread use in jurisdictions with inefficient regulations, as showcased in the 2016 Panama Papers, resulted in the collection of approximately $500 million in taxes and numerous criminal cases. The estimated annual cost of shell company exploitation (at $70 billion for the United States) underscores the imperative for businesses and authorities to maintain vigilance, implementing effective compliance strategies to identify and thwart financial crimes associated with these entities.
2. Committing Tax Evasion
Tax evasion entails a purposeful effort to evade tax obligations by either not declaring income or making fraudulent claims on tax returns. This differs from legal tax avoidance, which uses allowable strategies to minimize tax liability. Tax evasion involves illegal activities aimed at avoiding tax payments, potentially leading to substantial fines and imprisonment.
Tax authorities, including the Internal Revenue Service (IRS) of the U.S., employ diverse measures such as data analytics, audits, and investigations to identify and prevent fraudulent practices. Those involved in tax evasion may employ tactics like underreporting income, making false deductions, hiding assets offshore, or neglecting to file tax returns. Beyond the immediate legal consequences, tax evasion can have far-reaching effects on an individual's financial and professional standing, risking business licenses, credit scores, and future loan access. The broader societal impact is evident, depriving governments of essential resources required for funding crucial services.
The recent global focus on enhancing tax evasion laws highlights the need for collaborative efforts among law enforcement, tax authorities, and AML institutions to uphold principles of fairness, equality, and the integrity of the tax system.
3. Smurfing Transactions
Smurfing involves the careful division of a significant sum into smaller portions, skillfully crafted (for example, through the Cuckoo Technique) to evade the scrutiny of financial institutions and regulatory bodies. The essence of smurfing lies in introducing complexity; launderers engage in numerous smaller transactions designed to remain below reporting thresholds. These transactions span various channels, such as multiple bank deposits, wire transfers, or the acquisition of assets, creating an intricate web that conceals the origin of the funds.
The overarching objective is to avoid detection by authorities who typically focus on investigating larger, irregular financial activities. This covert practice not only challenges law enforcement efforts but also imposes broader consequences on financial institutions, regular customers, and societal trust in financial systems, necessitating robust countermeasures to mitigate its impact.
4. Interposing Cash-Intensive Businesses
Cash-intensive businesses, spanning various sectors like convenience stores, restaurants, and retail stores, often engage in legitimate activities but may be susceptible to money laundering or terrorist financing. For instance, a criminal might own a restaurant to launder currency from illicit activities, utilizing the business's legitimate cash flow to conceal unusual volumes.
The inherent difficulty in identifying such activities puts cash-intensive businesses at higher risk. To mitigate these risks, banks are advised to establish policies for identifying high-risk relationships, assess AML risks, conduct due diligence at account opening and periodically thereafter, and monitor these relationships for unusual or suspicious activity. This involves understanding the customer's business operations, the intended use of the account, and the associated geographic locations.
5. Gambling and Gaming
The gaming and gambling sectors have historically faced associations with money laundering and criminal activities. This association is more visible than ever in the sectors with a focus on online services. The industry's susceptibility to money laundering, given its high transaction volume and potential for anonymity, necessitates effective AML measures.
While some jurisdictions are reevaluating their stance due to revenue potential, stringent regulations persist. Robust AML policies remain imperative for gaming and gambling entities to mitigate financial crime risks and adhere to evolving regulatory demands. Implementing Know Your Customer (KYC) procedures, transaction monitoring, and suspicious activity reports (SARs) are key components. Identifying and managing AML risks, complying with regulatory obligations, and conducting independent audits further contribute to the industry's integrity and customer protection.
6. Utilizing Smugglers
Cash transportation has emerged as a favored method for terrorists to transfer funds, strategically evading traditional banking systems and circumventing the established AML and Countering the Financing of Terrorism (CFT) measures mandated by regulators. This technique represents one of the earliest forms of money laundering, involving the physical transport of cash across jurisdictions.
By sidestepping conventional financial channels, terrorists can operate beyond the reach of AML/CFT frameworks. The process entails physically moving the illicit funds from one location to another and subsequently depositing them in a bank or financial institution. This reliance on smuggling tactics underscores the adaptability of criminals in navigating regulatory constraints, posing significant challenges for authorities striving to curb illicit financial activities.
Innovative Solutions Against Defrauding
The importance of innovative solutions is underscored in countering defrauding activities, with AML software serving as a key player in this effort. By automating the detection process, AML software empowers financial institutions to stay ahead of fraudsters, protecting their assets and the overall integrity of the financial system. Furthermore, the adoption of cutting-edge AML solutions not only boosts the efficiency of compliance efforts but also ensures a proactive approach to risk mitigation.
Sanction Scanner's Fraud Detection Tool
Sanction Scanner stands at the forefront of AML software development, offering a cutting-edge Fraud Detection Tool that significantly enhances the efficiency of its Transaction Monitoring solution. Leveraging ready-to-use rules, this tool enables swift and seamless integration through APIs, allowing users to deploy the product within hours. The flexibility extends further, empowering users to create dynamic rules and scenarios tailored to their specific company needs. With a unique monitoring process that adapts to individual business requirements, Sanction Scanner ensures a customized approach to fraud detection.
Sanction Scanner empowers businesses to establish a unique and robust transaction monitoring process that aligns seamlessly with their operational requirements. To learn more, contact us or request a demo today.




